目录
- 抓包
- 对应用户sql
- Request Query 究竟是啥呢?
抓包
from core.mysql.models import ParseMonitoringDetail
from peewee import fn
from loguru import logger
group_by_parser_name: bool = True
group_by_error_class_name: bool = True
group_by_track_source_id: bool = True
query = (ParseMonitoringDetail
编程 .select(
ParseMonitoringDetail.parser_name,
ParseMonitoringDetail.error_class_name,
ParseMonitoringDetail.track_source_id,
fn.COUNT("*").alias('task_count')
)
.where(ParseMonitoringDehttp://www.devze.comtail.success == False)
.order_by(fn.COUNT("*").alias('task_count').desc()))
if group_by_parser_name:
query = query.group_by(
ParseMonitoringDetail.parser_name,
)
if group_by_error_class_name:
query = query.group_by(
ParseMonitoringDetail.error_class_name,
)
if group_by_track_source_id:
query = query.group_by(
ParseMonitoringDetail.track_source_id
)
logger.debug(f'sql: {str(query)}')
result = query.dicts().execute()
result = list(result)
logger.debug(result)
对应用户sql
执行上面的代码,对应用户的 sql 只有一个
SELECT
`t1`.`parser_name`,
`t1`.`error_class_name`,
`t1`.`track_source_id`,
COUNT('*') AS `task_count`
FROM
`parse_monitoring_detail` AS `t1`
jsWHERE
(`t1`.`success` = 0)
GROUP BY
`t1`.`track_source_id`
ORDER BY
`task_count` DESC
但是从 wireshark 抓包可以看到有多个 Request Query
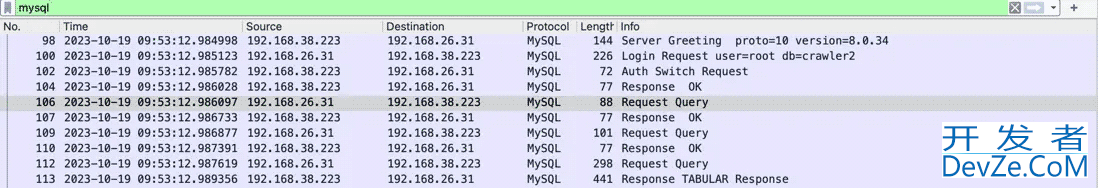
192.168.26.31 是客户端192.168.38.223 是 Mysql server
Request Query 究竟是啥呢?
第一个 Request Query
SET NAMES utf8mb4
第二个 Request Query
SET sql_mode='PIPES_AS_CONCAT'
第三个 Request Query
SELECT
`t1`.`parser_name`,
`t1`.`error_class_name`,
`t1`.`track_source_id`,
COUNT('*') AS `task_count`
FROM
`parse_monitoring_detail` AS `t1`
WHERE
(`t1`.`success` = 0)
GROUP BY
`t1`.`track_source_id`
ORDER BY
`task_count` DESC
以上就是peewee创建连接前的前置操作wireshark 抓包实现的详细内容,更多关于peewee连接前wireshark抓包的资料请关注编程客栈(www.编程cppcns.com编程)其它相关文章!




 加载中,请稍侯......
加载中,请稍侯......
精彩评论