I'm looking at the Linux IA-32 memory model of a process and I have a simple question to it. What do the grey areas in the picture contain? Are they only included to show the beginning and end of the memory? So, do text start at 0x0 and stack start at 0xFFFFFFFF?
Reopened: Hi, in an OS course I'm attending this question becomes relevant again. Specifically, I need to know what the grey areas contain. Based on the answers so far, I can see it contains kernel code in the top and a null-pointer dereference page in the bottom. But what is the kernel code? I don't assume it is the whole operating system itself,开发者_开发百科 but could it be embedded scheduler, kernel library calls or?
Best regards, Lasse Espeholt
alt text http://img403.imageshack.us/img403/3156/capturecj.png
I think this is more accurate:
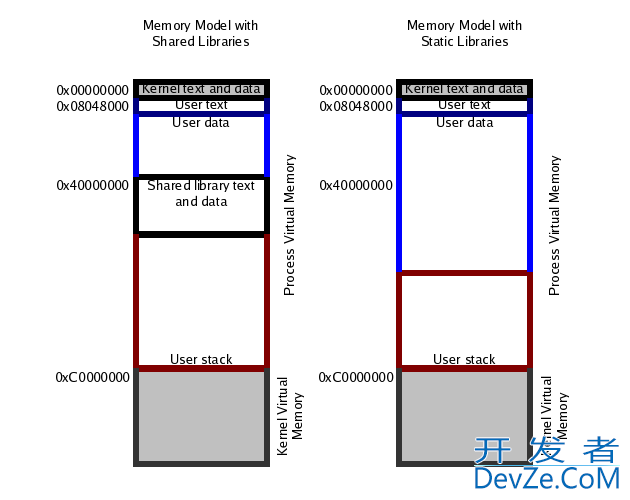
I think the grey areas simply represent regions of undefined size. Program text certainly wouldn't start at 0x0, because most OSes use them as invalid pages so null dereferences can be caught easily. Thread stacks also wouldn't go right up to 0xffffffff because usually the top quarter (or half) has kernel memory mapped into it.
Also note that due to address space layout randomization, the starting addresses of some of the sections are randomly offset from the values in the diagrams.
Nobody seems to have mentioned that not all memory in the available space is necessarily mapped (and it almost never is).
Note that the zero-page area at the bottom of the address space is not actually forbidden to application use under common linux distributions. The kernel used to do this, then ended up farming that decision out to the LSM module (e.g. SELinux, AppArmor). And they didn't enforce the same rule, so it turned out to be possible for processes to map memory at 0x0. This was part of the vulnerability behind the recent "kernel null pointer dereference" exploits.





![Interactive visualization of a graph in python [closed]](https://www.devze.com/res/2023/04-10/09/92d32fe8c0d22fb96bd6f6e8b7d1f457.gif)



 加载中,请稍侯......
加载中,请稍侯......
精彩评论